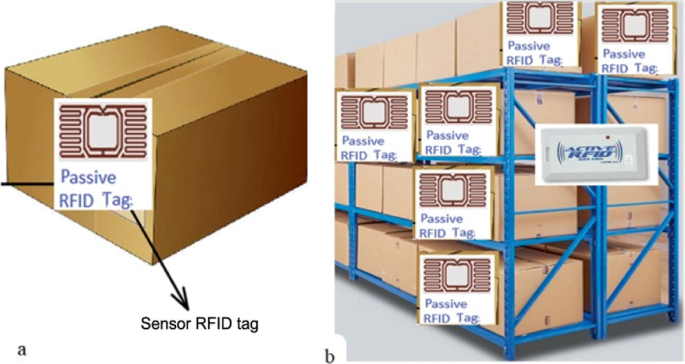
38 an rfid label on a box is an example of what type of physical security detection method?
In open system authentication how does authentication An RFID label on a box is an example of what type of physical security detection method? a. motion detection technologyb. video surveillance via CCTV c. tamper detectiond. asset tracking tagging 75. The combination of a public key and a private key are known by what term below?a. key set b. key teamc. key pair d. key tie 76. Using RFID for Inventory Management: Pros and Cons - Camcode The use of RFID for inventory management requires a scanner that uses radio waves to communicate with an RFID tag. The tag itself contains a microchip that allows the reader to read data and also write data to the tag for real-time updating in place. Each tag is wrapped in a material like plastic or paper for protection and can be affixed to a ...
How is a posture assessment performed on an - Course Hero An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging What statement regarding the different versions of the SHA hashing algorithm is accurate? a.

An rfid label on a box is an example of what type of physical security detection method?
What is Physical Security? Measures, Best Practices + PDF Guide Physical security is always a component of a wider security strategy, but it makes up a sizeable piece of this larger plan. Security experts agree that the three most important components of a physical security plan are access control, surveillance, and security testing, which work together to make your space more secure. quizlet.com › 344963834 › ch-9-quiz-cts1134-flash-cardsCh. 9 Quiz CTS1134 Flashcards | Quizlet principle of least privilege An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging How is a posture assessment performed on an organization? A thorough examination of each aspect of the organization's network is performed to determine how it might be compromised 6 Types of Warehouse Storage Systems - Camcode Mobile Shelving. Pallet Racking. Multi-tier Racking. Mezzanine Flooring. Wire Partitions. Read on to learn more about the 6 most popular warehouse storage system types. 1. Static Shelving. As the name suggests, static shelves are storage mechanisms that are designed to stay in one place.
An rfid label on a box is an example of what type of physical security detection method?. › subscribeSubscribe - RFID JOURNAL Only RFID Journal provides you with the latest insights into what’s happening with the technology and standards and inside the operations of leading early adopters across all industries and around the world. To stay informed and take advantage of all of the unique resources RFID Journal offers become a member today. What Is RFID Technology and How Can I Use It? - Shopify RFly, for example, created a drone that scans RFID tags and locates products inside a warehouse. If the item is stacked on a high shelf, the drone will collect it. With RFID-enabled drones, the health and safety risks of a factory worker are diminished. There's no need for them to use machinery or climb ladders to retrieve the item. FAQ Face Detection: Face Detection function is fulfilled by the camera. The face features such as eyes and mouth would be recognized. The detection highly demands the size of face shown in the image and the angle to the lens. We recommend users have the camera installed close to the desired detection region and make sure people face the camera directly. Notice: Face … Free Press Release Distribution Service - Pressbox 15.06.2019 · Free press release distribution service from Pressbox as well as providing professional copywriting services to targeted audiences globally
rSlaB $67 All editions Deluxe Edition 63 Find many great new & used options and get the best deals for Ruined King: A League of Legends Story Physical Collector's Edition SHIPS NOW at the There are 25 offers ranging from 28 There are 25 offers ranging from 28. Buy Ruined King A League of Legends Story Ruination Starter Pack CD Key Score: 88 /100 Released on November 16th, … en.wikipedia.org › wiki › Radio-frequency_identificationRadio-frequency identification - Wikipedia Often more than one tag will respond to a tag reader, for example, many individual products with tags may be shipped in a common box or on a common pallet. Collision detection is important to allow reading of data. Two different types of protocols are used to "singulate" a particular tag, allowing its data to be read in the midst of many ... US8085150B2 - Inventory system for RFID tagged objects - Google Patents A case for containing objects can include a Radio Frequency Identification (RFID) Reader antenna to detect any RFID tags placed within the case. The RFID antenna can operably connect with external RFID Reader components to detect RFID tags in the case. Alternately, a case can also include a passive RFID antenna to couple with any RFID tags in the case. How do RFID and RF tags work? - Explain that Stuff Photo: An example of the kind of RFID tag used in book labels. It helps with automated stock control and (in some systems) might double-up as an anti-theft device. You can often see these by holding library paperbacks up to the light. This tag is a UPM Raflatac RaceTrack that can hold up to 1 kilobyte (1024 characters) of information.
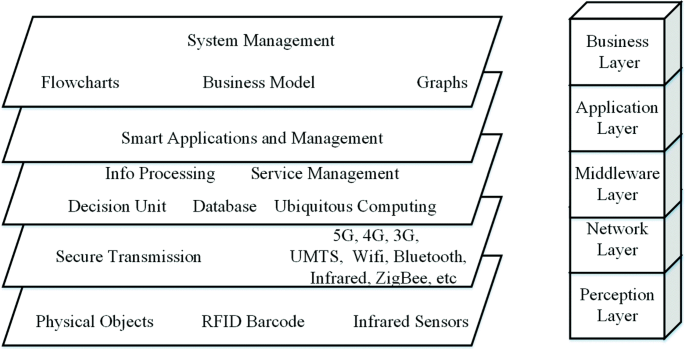
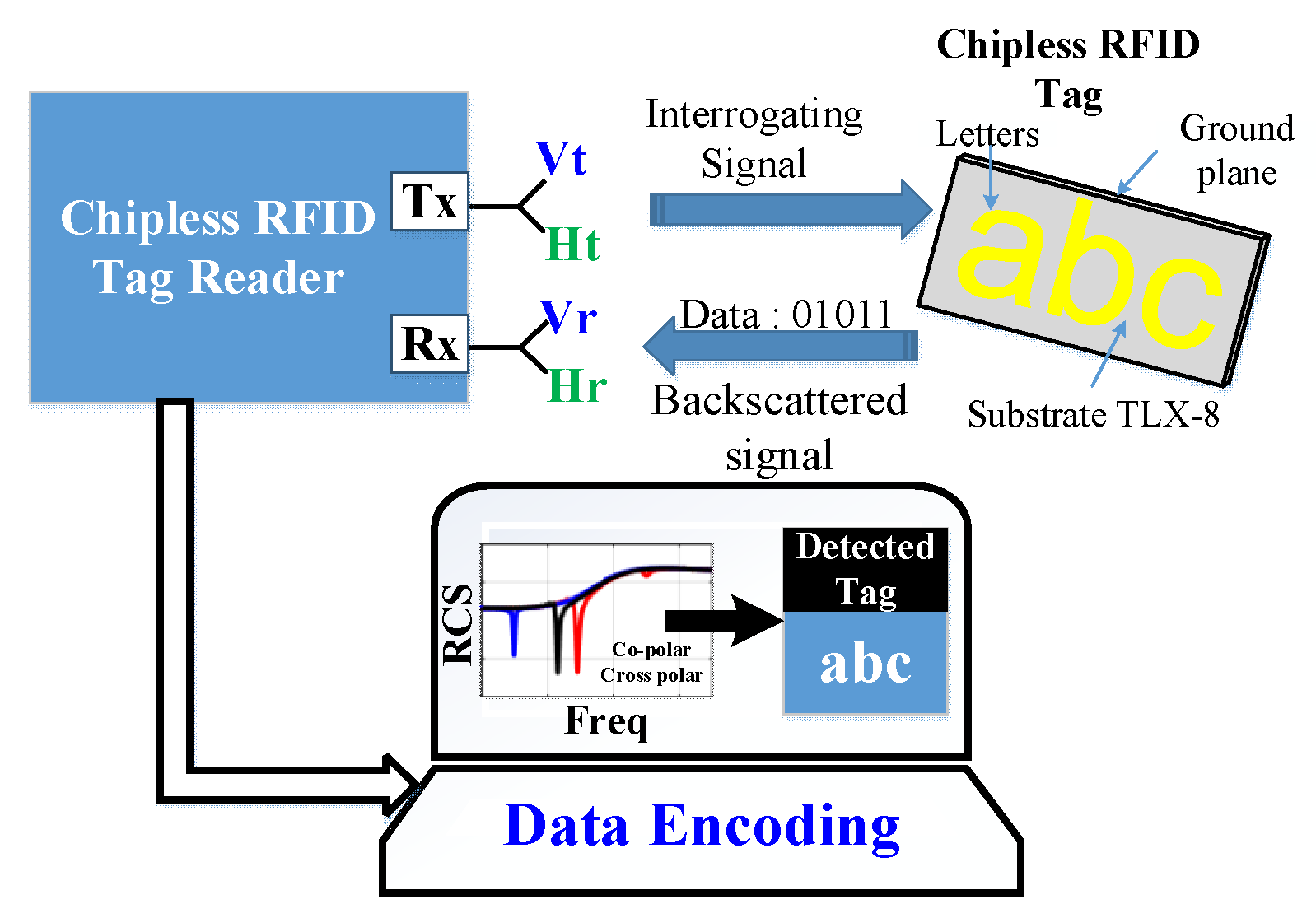
Authentication - Wikipedia Authentication is relevant to multiple fields. In art, antiques and anthropology, a common problem is verifying that a given artifact was produced by a certain person or in a certain place or period of history.In computer science, verifying a user's identity is often required to allow access to confidential data or systems.. Authentication can be considered to be of three types: US20060214789A1 - Tamper detection with RFID tag - Google Patents A sensor may be used to detect a previous or current change of state, and the change may be reported by a radio frequency identification (RFID) tag. In some embodiments, the change may represent a broken security seal, which in turn may affect an electrical connection that can be sensed by the RFID tag during operation of the RFID tag. link.springer.com › chapter › 10IoT Reference Model | SpringerLink Sep 06, 2013 · As we can see in Fig. 7.2, the important entities that are relevant for our use case are depicted with blocks of different colours.For instance, there is our truck driver “Ted” represented by as a yellow box (viz. instance), and the temperature sensor (that triggers an alarm after Ted had turned off the engine of the truck) is represented as a blue instance. What are RFID Tags, How Do They Work? - Camcode RFID tags are a type of tracking system that uses smart barcodes in order to identify items. RFID is short for "radio frequency identification," and as such, RFID tags utilize radio frequency technology. These radio waves transmit data from the tag to a reader, which then transmits the information to an RFID computer program.
Chapter 9 -- Network II Flashcards & Practice Test | Quizlet A) Polymorphic malware can change its characteristics every time it is transferred to a new system. B) Polymorphic malware is designed to activate on a particular date, remaining harmless until that time. C) Polymorphic malware is software that disguises itself as a legitimate program, or replaces a legitimate program's code with destructive code.
Ch 9: Network Risk Management Flashcards Preview - Brainscape An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging 20 What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths. 21
RFID Programming: Easy Guide for Beginners | Developer.com The RFID Hardware. RFID generally involves a reader and a set of tags. The reader scans a tag and pulls information from it. This information can be used to uniquely identify the tag and thus identify whatever is associated to the given tag. There are a variety of readers that can be used. These range from readers for passive tags to readers ...
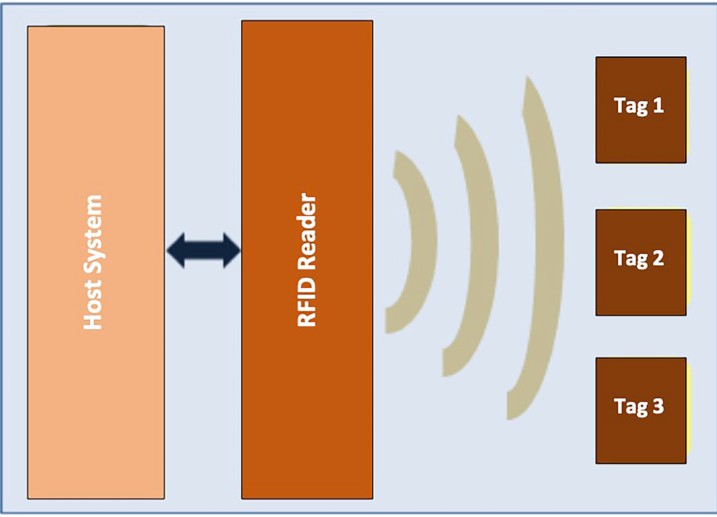
THE RFID TECHNOLOGY AND ITS APPLICATIONS: A REVIEW - ResearchGate Radio frequency identification (RFID) technology is an automatic recognition system that uses radio waves to identify products and objects. RFID system consists of a tag, a reader, and a ...
IoT Reference Model | SpringerLink 06.09.2013 · For example, even for the same type of user, unforeseen activity patterns in the physical world and thus unforeseen usage may arise may arise. For instance, errors are introduced into the system through explicit, erroneous management directives (Harrisburg, Chernobyl). Another example is that Devices can suddenly just die. The latter is most likely to …
Subscribe - RFID JOURNAL Only RFID Journal provides you with the latest insights into what’s happening with the technology and standards and inside the operations of leading early adopters across all industries and around the world. To stay informed and take advantage of all of the unique resources RFID Journal offers become a member today.
Press Release Distribution Service - Pressbox Jun 15, 2019 · Free press release distribution service from Pressbox as well as providing professional copywriting services to targeted audiences globally
Network+ 8th Edition Chapter 9 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging asset tracking tagging 12.
US8615473B2 - Method and system for anticipatory package A method and system for anticipatory package shipping are disclosed. According to one embodiment, a method may include packaging one or more items as a package for eventual shipment to a delivery address, selecting a destination geographical area to which to ship the package, shipping the package to the destination geographical area without completely …
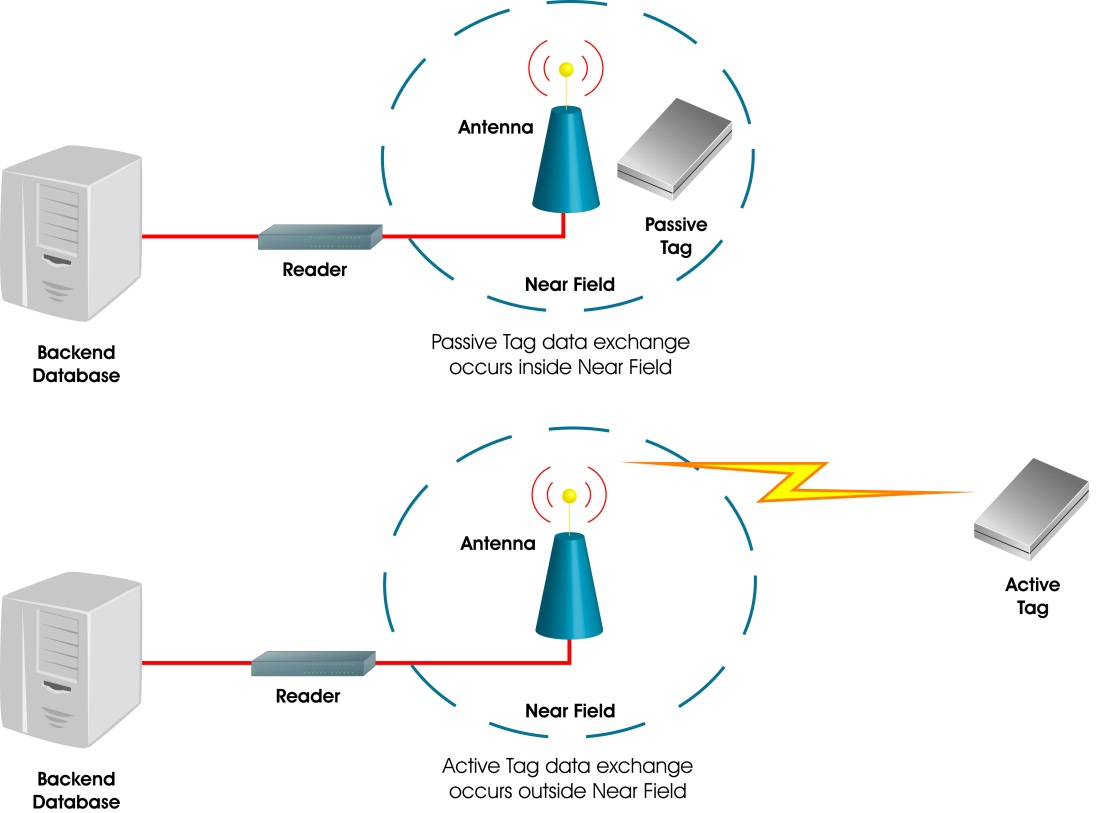
RFID is an acronym for "radio-frequency identification" and refers to a technology whereby digital data encoded in RFID tags or smart labels (defined below) are captured by a reader via radio waves. RFID is similar to barcoding in that data from a tag or label are captured by a device that stores the data in a database.
Chapter 9 Flashcards by Victor Mendez | Brainscape An RFID label on a box is an example of what type of physical security detection method? Asset tracking tagging 30 What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths 31
Chapter 1: Threats, Attacks, and Vulnerabilities - Quizlet What type of security team establishes the rules of engagement for a cybersecurity exercise? A. Blue team B. White team C. Purple team D. Red team. B. White teams act as judges and observers during cybersecurity exercises. Blue teams act as defenders, red teams act as attackers, and purple teams are composed of both blue and red team members to combine …
Ch9 network Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging. What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths. On a Linux based system, what command can you use to create a hash of a file using SHA-256? ...
quizlet.com › 604419533 › chapter-1-threats-attacksChapter 1: Threats, Attacks, and Vulnerabilities - Quizlet John is responsible for physical security at a large manufacturing plant. Employees all use a smartcard in order to open the front door and enter the facility. Which of the following is a common way attackers would circumvent this system? A. Phishing B. Tailgating C. Spoofing the smartcard D. RFID spoofing
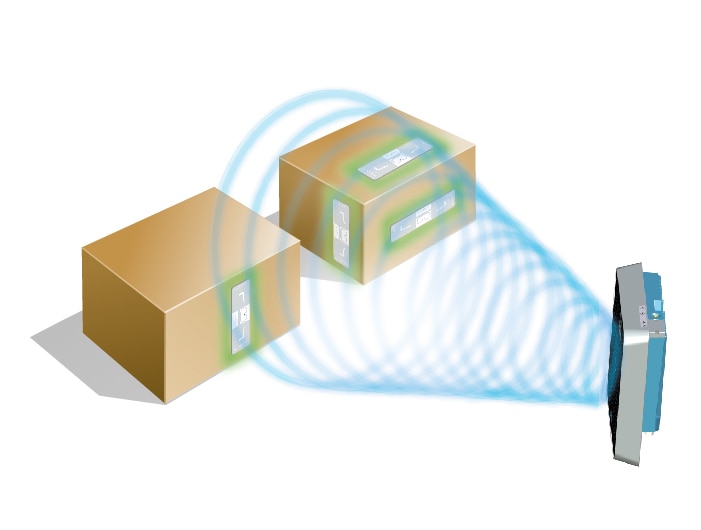
RFID Know-How: Identification using RFID technology | SICK Radio Frequency Identification (RFID) is a technology that uses radio waves to automatically identify objects. It is based on an RFID system, which comprises an RFID reader (1) and an RFID transponder (2). The transponder is located directly on the object to be identified, while the RFID reader contactlessly reads the data stored on the ...
US7360714B2 - Label and RFID tag issuing apparatus - Google Patents A label and RFID tag issuing apparatus comprises a recording apparatus that records information on a production label and an RFID tag reader/writer that writes and reads part of the recorded information to/from an RFID tag. This label and RFID tag issuing apparatus writes a production number to the RFID tag attached to the container if a container for containing an article or articles carrying ...
Radio Frequency Identification (RFID) | FDA Active RFID tags are powered by batteries. RFID tags can store a range of information from one serial number to several pages of data. Readers can be mobile so that they can be carried by hand, or...
Ch. 9 Quiz CTS1134 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging. How is a posture assessment performed on an organization? A thorough examination of each aspect of the organization's network is performed to determine how it might be compromised. What statement regarding denial-of-service (DoS) attacks is accurate? A …
Question28 11pts what type of door access control is - Course Hero key fob lock Question 29 1 / 1 pts An RFID label on a box is an example of what type of physical security detection method? Correct! asset tracking tagging video surveillance via CCTV tamper detection motion detection technology asset tracking tagging
en.wikipedia.org › wiki › AuthenticationAuthentication - Wikipedia The second type of authentication is comparing the attributes of the object itself to what is known about objects of that origin. For example, an art expert might look for similarities in the style of painting, check the location and form of a signature, or compare the object to an old photograph.
Free Computers Flashcards about Chap 9 and 10 Quiz - StudyStack An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging: What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths.
What is RFID? | The Beginner's Guide to How RFID Systems Work An RFID inlay or label is a common example of a recurring cost in an RFID system. Because of their low-cost, these tags are frequently applied once and kept on an item for its lifespan (or discarded after use). If an RFID printer is used, then printer ribbon would also be a recurring cost.
Network+ 8th Edition Chapter 9 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging d. asset tracking tagging 12.
8.docx - 39. With VTP, where is the VLAN database stored?... An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging44. An attack that relies on redirected and captured secure transmissions as they occur is known as what type of attack? man-in-the-middle attack 45. How often should you require users to change their passwords? every 60 days 46.
Radio-frequency identification - Wikipedia Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter.When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, …
6 Types of Warehouse Storage Systems - Camcode Mobile Shelving. Pallet Racking. Multi-tier Racking. Mezzanine Flooring. Wire Partitions. Read on to learn more about the 6 most popular warehouse storage system types. 1. Static Shelving. As the name suggests, static shelves are storage mechanisms that are designed to stay in one place.
quizlet.com › 344963834 › ch-9-quiz-cts1134-flash-cardsCh. 9 Quiz CTS1134 Flashcards | Quizlet principle of least privilege An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging How is a posture assessment performed on an organization? A thorough examination of each aspect of the organization's network is performed to determine how it might be compromised
What is Physical Security? Measures, Best Practices + PDF Guide Physical security is always a component of a wider security strategy, but it makes up a sizeable piece of this larger plan. Security experts agree that the three most important components of a physical security plan are access control, surveillance, and security testing, which work together to make your space more secure.

























Post a Comment for "38 an rfid label on a box is an example of what type of physical security detection method?"